

DRM Security Best Practices
February 20, 2025
Introduction
Video and streaming businesses turn to Digital Rights Management (DRM) to secure their content, but simply adding DRM is not enough. The effectiveness of DRM depends on how it is implemented and how well it is integrated into a broader security strategy. Poor implementation can lead to vulnerabilities that pirates exploit, negating DRM’s intended purpose. This article highlights best practices to maximize DRM security and avoid common pitfalls.
Industry Standards & Recommendations
The industry collaborates to improve video security. Organizations like the Streaming Video Technology Alliance (SVTA) and MovieLabs publish best practices and guidelines to help businesses strengthen their security measures. For example:
-
OTT Streaming Security Checklist - March 2024
-
OTT Streaming CDN Security Best Practices - soon to be published
-
Specification for Enhanced Content Protection - v1.4, August 2024
Following these standards ensures a more robust protection strategy and keeps companies aligned with the latest security trends and compliance requirements.
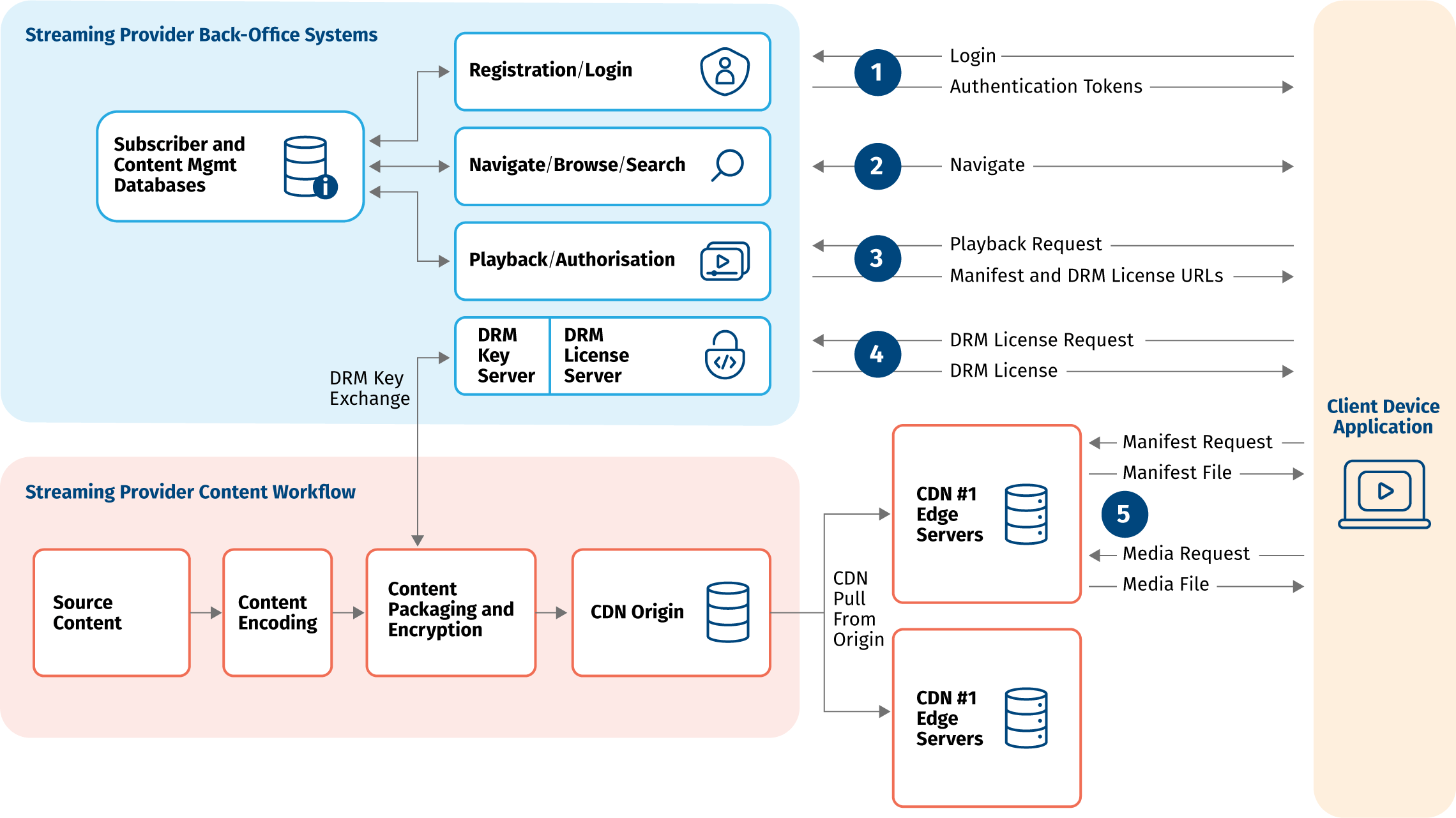
Authorization & Access Control
To ensure that only authorized users can access content, businesses should implement strict entitlement and licensing measures. This prevents unauthorized users from obtaining and sharing content illicitly.
DRM interactions are typically split into two steps:
-
Playback Request - client asks for a permission to play a specific content and receives an authorization token used for a subsequent DRM License Request. In Axinom DRM, this is called "entitlement message"
-
DRM License Request - client provides the authorization token and receives a DRM License that allows the playback of the content using specific DRM technology
Limit authorization to a specific key (or set of keys)
Instead of allowing broad access to multiple content keys, restrict authorization to only the necessary encryption keys associated with the requested media.
Use unique content encryption keys for each asset
Each video asset should have its own encryption key to prevent widespread content leaks in case of a breach. This ensures that even if one key is compromised, it does not provide access to all content.
Restrict the lifespan of authorization tokens
Implementing short-lived access tokens reduces the risk of unauthorized use by limiting the time frame within which they can be exploited. The life time of the authorization token should be just enough to allow the client to obtain the DRM license.
Bind authorization to users and devices
Include as much client information as possible to the authorization token (for example, IP-address, device IDs, user ID) to prevent unauthorized sharing and reusing of the tokens.
Understanding CDMs and device security levels
A Content Decryption Module (CDM) is a secure component in a DRM client device that decrypts protected media while enforcing content usage policies, such as playback restrictions, output controls, and copy protection. CDMs ensure that only authorized users using compliant devices can access encrypted content, preventing unauthorized distribution and piracy. They work by securely handling decryption keys and applying DRM policies.
Security Levels in CDMs indicate the level of protection a device offers against attacks. Lower security levels typically rely on software-based decryption, which is more vulnerable to tampering, making it potentially easier for attackers to extract encryption keys. In contrast, higher security levels often require hardware-backed protection, such as Trusted Execution Environments (TEE) or Secure Media Paths (SMP), which provide stronger resistance against reverse engineering and key extraction. Content providers often mandate minimum security levels for accessing premium content, such as requiring hardware-backed CDMs for HD or UHD playback while allowing software-based CDMs for lower-value content like SD.
Enhancing Content Protection
While DRM provides a foundational layer of protection, additional measures should be taken to strengthen content security further.
Apply Proper DRM Policies
DRM policies define how a client can use the received DRM licenses (and enforced by client’s CDM). DRM policies should be aligned with business needs, such as restricting playback to secure environments, disabling unauthorized recording tools, and ensuring compliance with licensing agreements.
Higher-value content, such as HD and UHD videos, should have stricter security requirements than lower-resolution versions. For example, requiring hardware-secured decryption for premium content ensures a higher level of protection.
Note, that DRM policies are specific to the DRM technology used (such as Widevine, PlayReady or FairPlay).
Use unique content encryption keys for each video profile
A video asset typically includes multiple video profiles (SD, HD, UHD) and audio. It’s considered a best practice (and often even as a requirement by the content owners) to apply different DRM policies for different video profiles, i.e. setting stricter requirements for more valuable content, e.g. for HD / UHD resolutions or HDR versions.
To achieve this, you must encrypt each video profile (and audio) with a separate key. In the entitlement message, you will include multiple policies and refer for each key to the respective policy. You should restrict (in the entitlement service) which keys you provide to a given user depending on the properties of the user and their device (for example, only deliver HD to a user with premium subscription or only deliver UHD keys to devices which actually support UHD).
Strengthening DRM Operations
Implementing DRM goes beyond setting up encryption and licensing. A robust DRM strategy requires continuous monitoring, adaptation, and improvement.
Implement strong authorization logic
Ensure that only authorized users with valid subscriptions or purchases can access protected content. Multiple factors can be considered during authorization, such as:
-
Asset availability
-
Asset’s licensing window
-
Authentication status of the user
-
User’s subscription status (for premium content)
-
Geo-restrictions
-
Client’s device and its capabilities
Protect secrets
Secure any secrets used in the DRM chain. Exposure of these keys can allow attackers to generate valid authorization and license requests.
Use DRM Proxy Mode
In a proxy mode, all license requests go to the entitlement service, which acts as a proxy between the client and the DRM license service. In this scenario, the client never directly communicates with the DRM license service, which adds an extra layer of security.
Monitor logs for security insights
Regularly analyzing DRM license requests can help detect unusual activity, identify potential security breaches, and respond to threats in real-time. Also the entitlement service should keep a log, which should be regularly analyzed.
Conclusion
DRM is a powerful tool for content protection, but its effectiveness relies on proper implementation. By following best practices — such as controlled access, strong encryption policies, and proactive monitoring — businesses can significantly reduce the risk of piracy and content leaks.
However, DRM alone is not a silver bullet. A multi-layered approach that includes user authentication, secure distribution channels, watermarking, and continuous security assessments is essential for long-term success. By adopting these best practices and staying updated with industry standards, businesses can maximize the benefits of their DRM solutions and ensure their valuable content remains protected.
Safeguard your content with a free 60-day trial of Axinom DRM to implement the best security practices - Get started now!








